You are probably well aware of the most popular Portscanner Nmap, but did you know that you can also use Netcat to do basic portscans? Today I will show you how to scan for open ports with Netcat. You probably have used Nmap before and appreciate it’s capabilities.
Yet, if you just want to run a quick and basic Portscan, you can also use the good old Netcat command for it. In this example, we will utilize Metasploitable2 as a victim and try to scan its open ports using Netcat.
Scan for Open Ports using Netcat
To do a portscan we use the following command.
nc -z -v 192.168.1.103 1-443
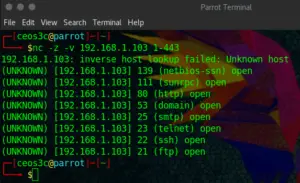
The Portscan finishes almost immediately. A quick rundown of the options:
- nc = netcat
- -z = Portscanning mode or zero I/O mode
- -v = verbose mode
- 192.168.1.103 = the IP of your target
- 1-443 = The port range we want to scan
As you can see, this is a nice and quick alternative to run a quick portscan directly with Netcat.
There is no specific advantage to use it over Nmap, just that in my experience it can be a little faster. If course, it is not as precise as an intense Nmap scan. So this is really just for running a Portscan in a very short amount of time. It is always good to have more than one tool at ones disposal.
It happened many times to me that a certain tool wasn’t working as expected and I had to dig out something else to get the job done. So, the more tools you have at your disposal, the better you are off.
To continue this tutorial, I have written another one on how to scan protocol versions using Netcat. Check it out of you want to learn more.
Until next time.
https://www.youtube.com/watch?v=41RULvvjo4A

