Now that you know how to work with Advanced Nmap commands as shown in the article on Advanced Nmap Commands we now can go ahead and tackle the next topic. In this article, we will go more deeply into Nmap and explore that Nmap is not just a port scanner that only scans ports on the target machine, but it contains a Nmap Scripting Engine (NSE) which has pre-made Nmap scripts to dig further into the system. The Nmap Scripting Engine extends the capabilities of Nmap which enables it to perform a variety of operations and report the results of Nmap scripts with regular output. Some examples of NSE scripts include:
- Enhanced Network Lookup: WHOIS lookup, Traceroute, Samba file share discovery, and additional protocol queries
- Advanced Version Detection Capability: Complex probing to detect the version of the target.
- Bruteforce: Can discover the authentication mechanism in the service and brute forces it with a Nmap script.
- Vulnerability Detection: Checks for the vulnerability of services accordingly to their functionalities and versions.
- Malware Detection: Having the capability to discover trojans and worm backdoors.
- Vulnerability Exploitation: Exploits the significant and common vulnerabilities on the go.
These Nmap scripts are written in the LUA programming language and named with the extension .nse. You can even download a third-party custom-made script that can run with Nmap. In Linux and Unix, the default storage location is the /usr/share/nmap/scripts subdirectory while in Windows, the default location is C:\Program Files\Nmap\scripts.
Note: If you want to use Nmap on Windows without the need of installing bare-metal Linux or a virtual machine utilizing the power of WSL 2, we have an entire tutorial series covering how to do that.
Table of Contents
👀 This Tutorial has some related Articles!
👉 Part 1 – Nmap Basics
👉 Part 2 – Nmap Host Discovery
👉 Part 3 – Advanced Nmap Commands
👉 Part 4 – Nmap NSE Scripts
👉 Part 5 – Nmap on Windows
NSE Scripts Overview
The basic syntax for executing an NSE script is:
nmap --script <scriptname> <host ip>Code language: HTML, XML (xml)| Command | Option |
| –script default | Default Scan |
| –script external | Scan by External Sources |
| –script discovery | Discovery Scan |
| –script safe | Safe Scan |
| –script vuln | Common Vulnerability Scan |
| –script auth | Authentication Scan |
| –script broadcast | Broadcast Scan |
| –script exploit | Exploit Scan |
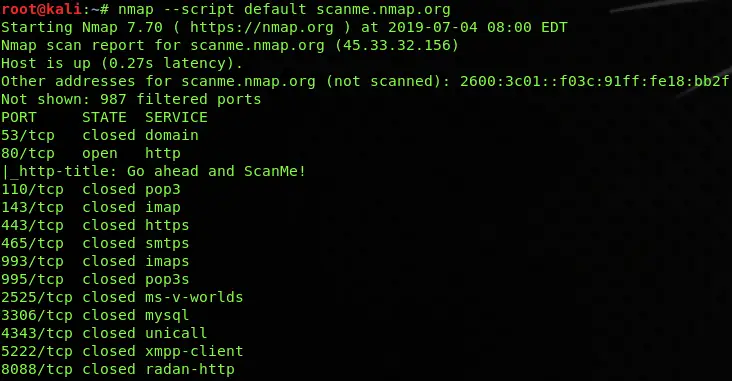
Default NSE Scan
nmap --script default scanme.nmap.orgCode language: CSS (css)A default script is a group of scripts that runs a bunch of individual analysis scripts at once. They are used to expose the necessary information related to the operating system like the workgroup name, the NetBIOS names, FTP bounce check, FTP anonymous login checks, SSH checks, DNS discovery and recursion, clock skew, HTTP methods, rpcinfo, VNC info, SSL check, etc.
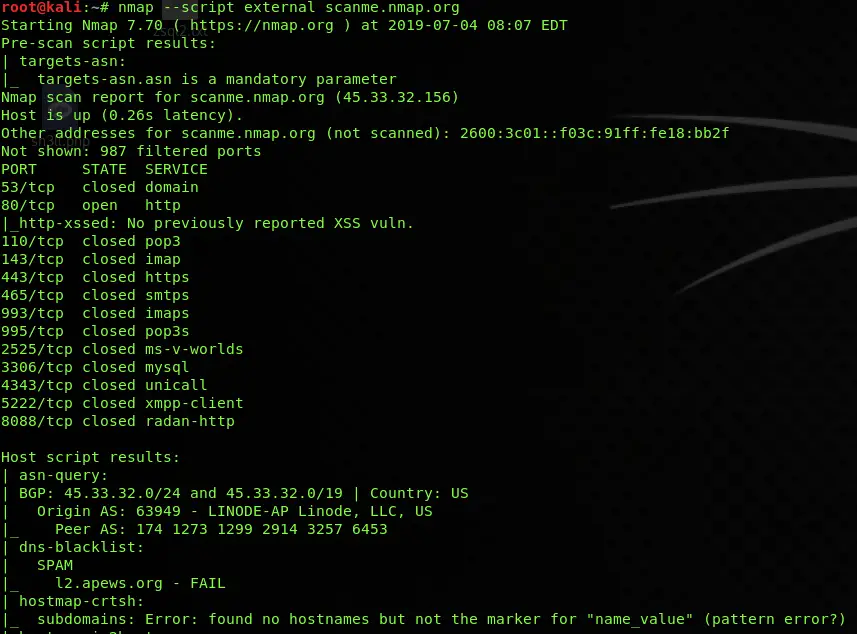
External Scan
nmap --script external scanme.nmap.orgCode language: CSS (css)The external script is a group of scripts that runs multiple individual Nmap scripts at once and checks the access and status of services running on the target by using external testing services which includes DNS discovery, HTTP Cross-Domain policy, XSSed database searches, CVSS checks for known vulnerabilities, TOR node checks, SMTP open relay checks, Shodan searches, Geo-location of IP address, and etc.
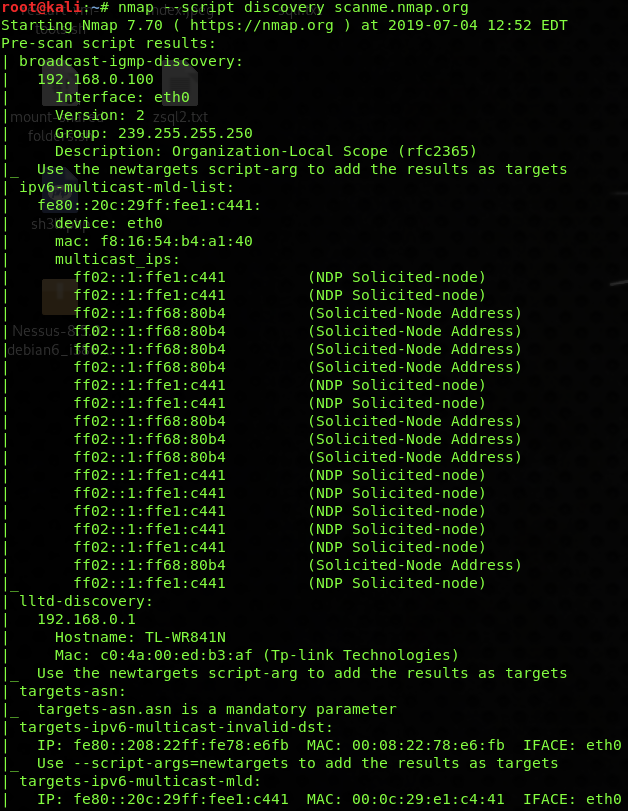
Discovery Scan
nmap --script discovery scanme.nmap.orgCode language: CSS (css)Discovery scripts are ideal when you need to have as much information as possible about your remote target. This category of Nmap scripts is used to perform banner grabbing, cics information, Citrix enumeration, DNS zone check, HTTP user-agent testing, icap information, MS SQL configuration, SMB enumeration, etc.
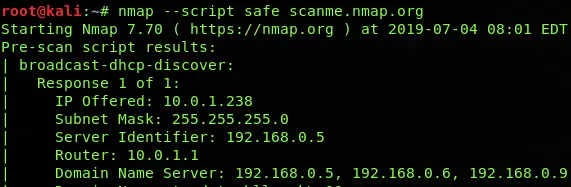
Safe Scan
nmap --script safe scanme.nmap.orgCode language: CSS (css)A safe script is a group of less intrusive NSE scripts which makes low noise while using them against the remote system. They are used to perform DNS enumeration, DHCP discovery and recursion, HTTP index page finding, finding software versions, HTTP TRACE, IP forwarding checks, IRC info, NFS mounting, etc.
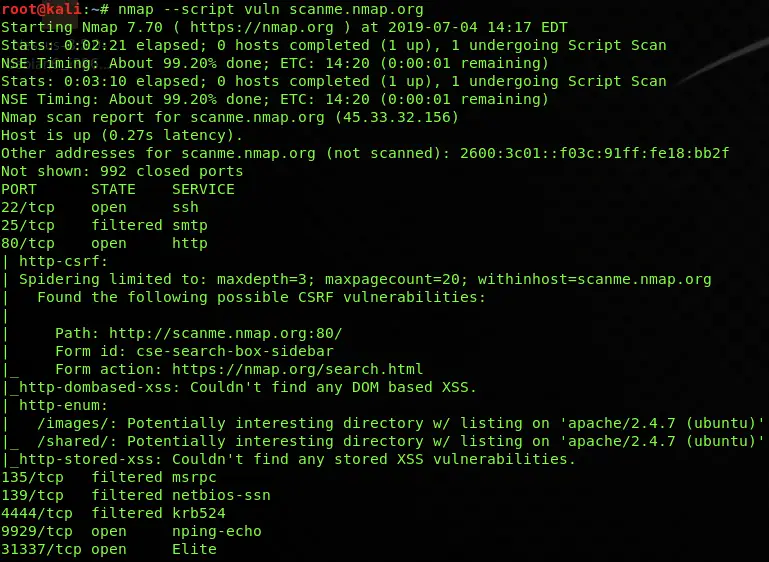
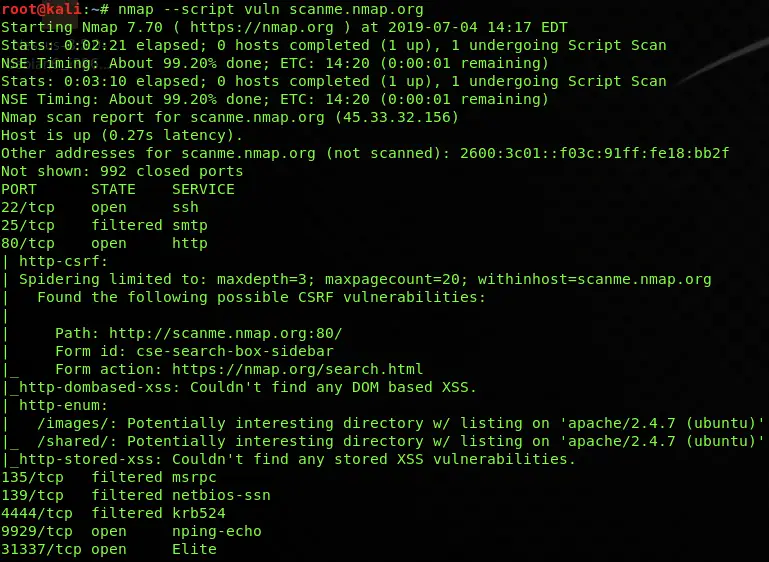
Vulnerability Scan
nmap --script vuln scanme.nmap.orgCode language: CSS (css)Vulnerability scanning is also a part of NSE scripts which are used to check and find some of the most common vulnerabilities on your target host. The types of vulnerabilities it can find include HTTP slowloris, Apache Range DOS header, FTP bounce, anonymous login, XSS, Shellshock, SQL injection, CVE, 2010-2861, CVE 20111-3368, etc.
I personally use this Nmap script all the time, as it often discovered vulnerabilities for me in the past.
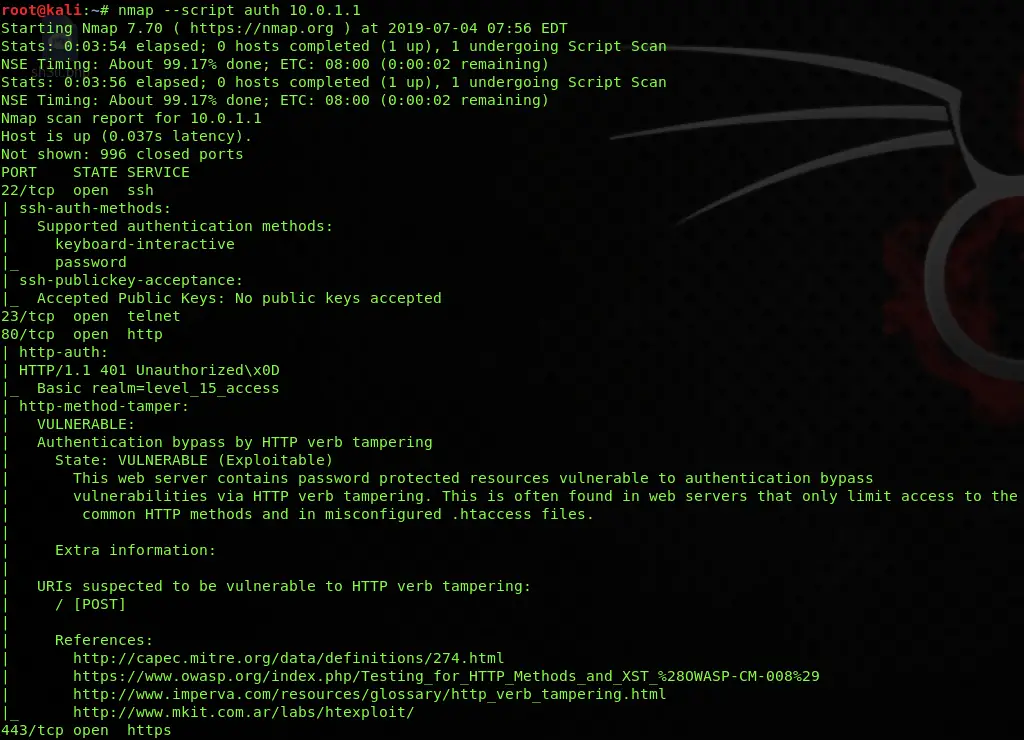
Authentication Scan
nmap --script auth scanme.nmap.orgCode language: CSS (css)An auth script scan is a group of scripts which are used to check the authentication mechanism of different services which includes AJP login checks, user enumeration through brute force, X11 server access, SSH authentication, VNC login bypass, MySQL users and hashes, WordPress user enumeration, default login checks, etc.
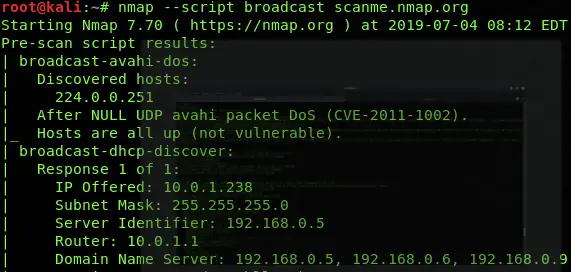
Broadcast Scan
nmap --script broadcast scanme.nmap.orgCode language: CSS (css)The broadcast script runs multiple Nmap scripts at once which checks for the queries of multicast routing protocols, resolves the hostname, checks for hosts on the local network, triggers Wake on LAN, checks for Avahi DOS, search for SQL servers, EIGRP discovery, etc.
Exploit Scan
nmap --script exploit scanme.nmap.orgCode language: CSS (css)This type of scan has one of the most potent Nmap scripts as it can be able to exploit potential services running on the remote host. It can exploit vsftpd backdoors, HTTP file upload exploits, Litespeed source code downloads, SMB exploitation, UnrealIRCD backdoors, CVE 2013-7091, CVE 2017-5689, etc.
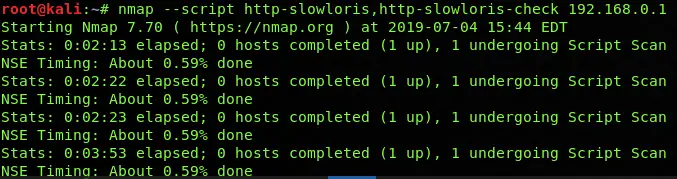
Run multiple NSE scripts
You can also run multiple NSE scripts at once by using the following syntax:
nmap --script <scriptname>,<scriptname>, <host ip>Code language: HTML, XML (xml)The primary purpose of running multiple scripts is to perform the recursive function or to double-check to validate the result if it is genuinely positive or a false positive, as shown in the above screenshot. The reason for this would be to confirm that the HTTP slowloris vulnerability really exists, then exploit it in the same run. You can also run the individual scripts by selecting them manually from the default install location, as mentioned at the start of the article.
👀 This Tutorial has some related Articles!
👉 How to get started in Cyber Security – The Complete Guide
👉 How to get started with Bug Bounties
👉 Terminal Customization Series
👉 Best Ethical Hacking Books
👉 Download Kali Linux Safe & Easy
👉 Best Ethical Hacking Tools
👉 Install VSCode on Kali Linux
👉 Dual Boot Kali Linux with Windows
👉 Install Kali Linux on VirtualBox – Complete Beginner Guide
👉 Top Things to do after installing Kali Linux
👉 WiFi Adapter for Kali Linux – The Ultimate Guide
👉 Nmap Beginner Guide Series
👉 Metasploit Tutorial Series
👉 Burp Suite Beginner Guide
My favorite Nmap Scripts
My favorite NSE scripts are two scripts that are not included in a basic Nmap installation. The scripts are Nmap-Vulners and Vulscan. Both of those scripts are third-party scripts and they both use CVE records to improve Nmap’s version detection capabilities. The scripts will use this information to show you known CVE’s that are exploitable. Both those scripts are a topic on their own, which will be covered in a separate article, but I will quickly show you how to install and how to use them, so you can play around with them.
Installing Nmap-Vulners
First, you need to navigate to the Nmap Scripts folder:
cd /usr/share/nmap/scripts/From here, you need to clone the Nmap-Vulners Git repository:
git clone https://github.com/vulnersCom/nmap-vulners.gitCode language: PHP (php)Installing Vulscan
Make sure you are still inside of the Nmap Scripts folder:
cd /usr/share/nmap/scripts/Also, clone the Git repository:
git clone https://github.com/scipag/vulscan.gitCode language: PHP (php)Updating the Vulscan database:
cd vulscan/utilities/updater
chmod +x updateFiles.sh
./updateFiles.sh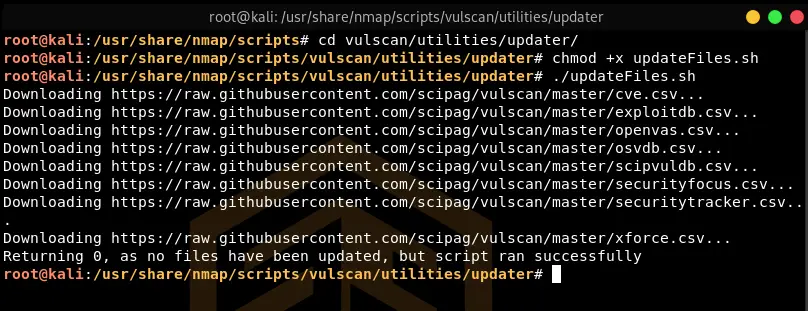
Using Nmap-Vulners
As with the other Nmap scripts, the usage is pretty similar, except that the -sV tag is mandatory. -sV is scanning for version information, which is crucial for Vulners to work.
nmap --script nmap-vulners -sV <target-ip>Code language: HTML, XML (xml)Using Vulscan
The syntax to use Vulscan is pretty similar.
nmap --script vulscan -sV <host-ip>Code language: HTML, XML (xml)Of course, you can also combine Nmap-Vulners and Vulscan into one command as shown in the example above. More on those two scripts in a separate article.
Updating NSE Database
nmap --script-updatedb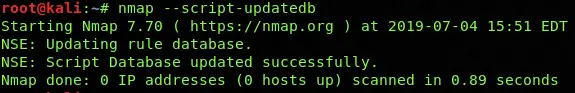
The nmap scripts database should be frequently updated to make sure to always have the most up-to-date scripts available.
Conclusion
The Nmap Scripting Engine gives much more power to Nmap above its usual use-case of being a port scanner. The Nmap scripts provide more enhanced and interesting results which can be used to collect and analyze more information about the remote host. The only drawback of NSE is that it takes more time in providing the results while on the other hand, the advantage is to easily run multiple scripts at once without tangling into hundreds of scripts.
👀 This Tutorial has some related Articles!
👉 Part 1 – Nmap Basics
👉 Part 2 – Nmap Host Discovery
👉 Part 3 – Advanced Nmap Commands
👉 Part 4 – Nmap NSE Scripts
👉 Part 5 – Nmap on Windows




Nice tutorial how to get updates in mail when you post these tutorials?
Hi Javed,
you can either sign up for the Newsletter (sidebar) or subscribe to my Reddit Channel (https://www.reddit.com/r/ceos3c), I always post new articles there!