Time to tackle the third part of the Nmap Tutorial Series. After covering Nmap Basics and Nmap Host Discovery, we are going to look at some more advanced Nmap commands. Sometimes it is necessary to perform scans that will do something else than the TCP scan that Nmap is doing by default. Those more advanced commands are used to detect exotic services or to evade firewalls.
Note: If you want to use Nmap on Windows without the need of installing bare-metal Linux or a virtual machine utilizing the power of WSL 2, we have an entire tutorial series covering how to do that.
Table of Contents
- Advanced Nmap Commands Overview
- TCP SYN Scan (-sS)
- TCP Connect Scan (-sT)
- UDP Scan (-sU)
- TCP NULL Scan (-sN)
- TCP FIN Scan (-sF)
- Xmas Scan (-sX)
- TCP ACK Scan (-sA)
- IP protocol Scan (-sO)
- SCTP Cookie Echo Scan (-sZ)
- Idle Scan (-sI)
- Conclusion
👀 This Tutorial has some related Articles!
👉 Part 1 – Nmap Basics
👉 Part 2 – Nmap Host Discovery
👉 Part 3 – Advanced Nmap Commands
👉 Part 4 – Nmap NSE Scripts
👉 Part 5 – Nmap on Windows
Advanced Nmap Commands Overview
First, let’s have an overview of all the advanced Nmap commands.
| Command | Option |
|---|---|
| -sS | TCP SYN Scan |
| -sT | TCP Connect Scan |
| -sU | UDP Scan |
| -sN | TCP NULL Scan |
| -sF | TCP FIN Scan |
| -sX | Xmas Scan |
| -sA | TCP ACK Scan |
| -sO | IP Protocol Scan |
| -sZ | SCTP COOKIE ECHO Scan |
| -sl | Idle Scan |
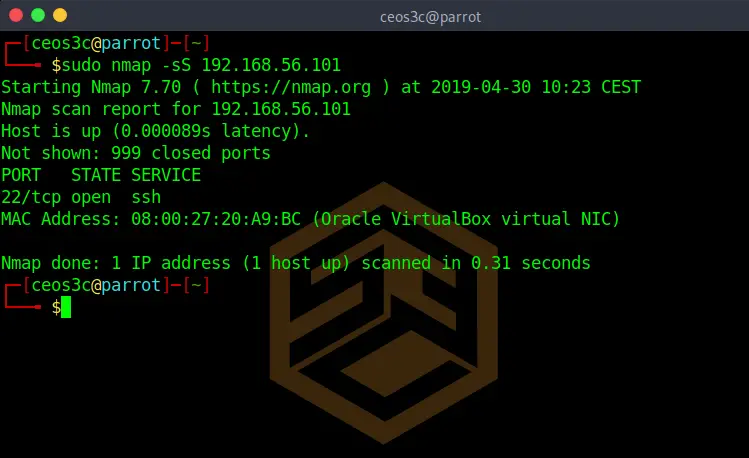
TCP SYN Scan (-sS)
sudo nmap -sS 192.168.56.101Code language: CSS (css)This scan scans for the 1000 most used TCP ports by sending SYN packages to a target and awaiting a response. This Nmap command is more on the stealthy side of things because it doesn’t try to connect to the target, you might be able to avoid being detected when using this command. I say might because it highly depends if the network has an IDS (Intrusion Detection System) in place or not.
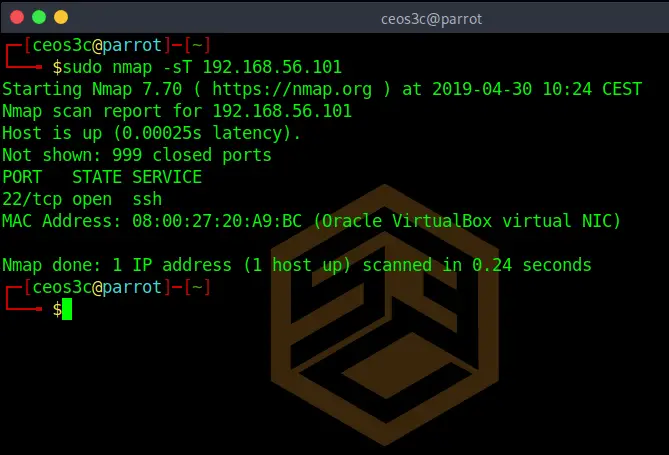
TCP Connect Scan (-sT)
nmap -sT 192.168.56.101Code language: CSS (css)The TCP Connect scan can be run without sudo, it attempts to establish a plain connection to the target host. This command is noisy, so use it with caution.
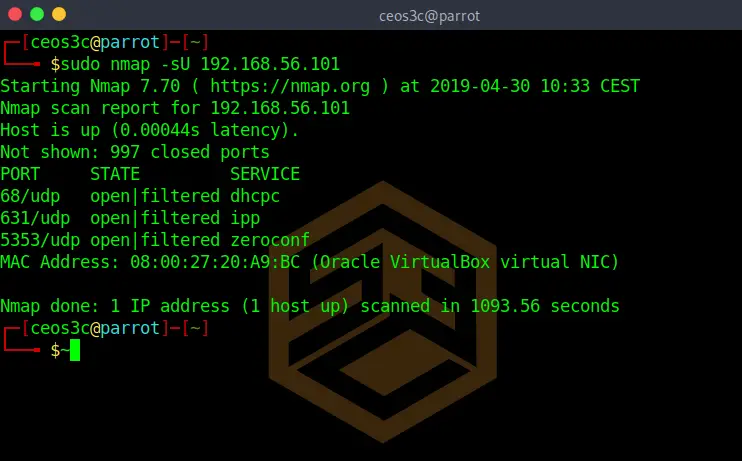
UDP Scan (-sU)
sudo nmap -sU 192.168.56.101Code language: CSS (css)The UDP Scan is a valuable asset for scanning services that use UDP like DNS and DHCP. I always run a UDP scan to find all the services that don’t use TCP.
👀 This Tutorial has some related Articles!
👉 How to get started in Cyber Security – The Complete Guide
👉 How to get started with Bug Bounties
👉 Terminal Customization Series
👉 Best Ethical Hacking Books
👉 Download Kali Linux Safe & Easy
👉 Best Ethical Hacking Tools
👉 Install VSCode on Kali Linux
👉 Dual Boot Kali Linux with Windows
👉 Install Kali Linux on VirtualBox – Complete Beginner Guide
👉 Top Things to do after installing Kali Linux
👉 WiFi Adapter for Kali Linux – The Ultimate Guide
👉 Nmap Beginner Guide Series
👉 Metasploit Tutorial Series
👉 Burp Suite Beginner Guide
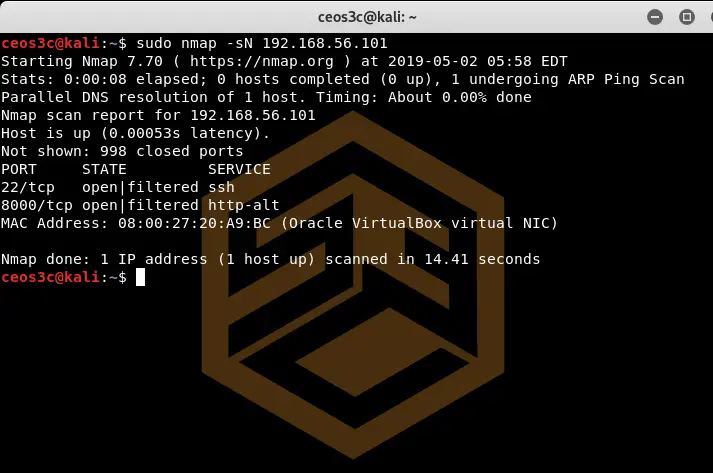
TCP NULL Scan (-sN)
sudo nmap -sN 192.168.56.101Code language: CSS (css)The TCP NULL Scan sends packets without TCP flags. This method is used to get the firewall to respond to the scan.
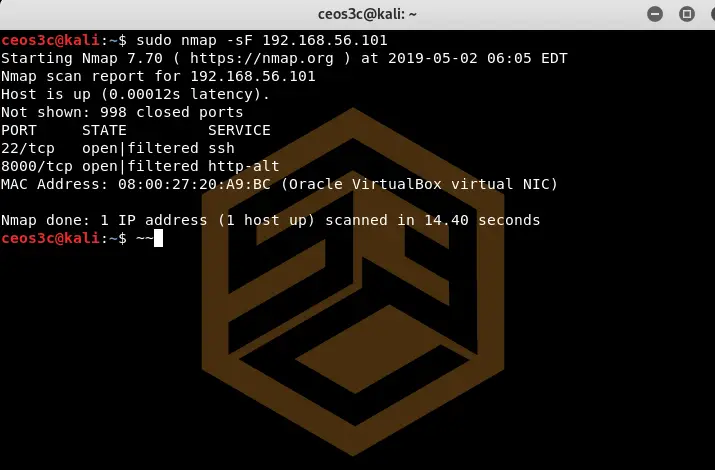
TCP FIN Scan (-sF)
sudo nmap -sF 192.168.56.101Code language: CSS (css)The TCP FIN Scan is used to get a TCP ACK response from the target. This is just another way to get around a firewall and trigger a response from the target host.
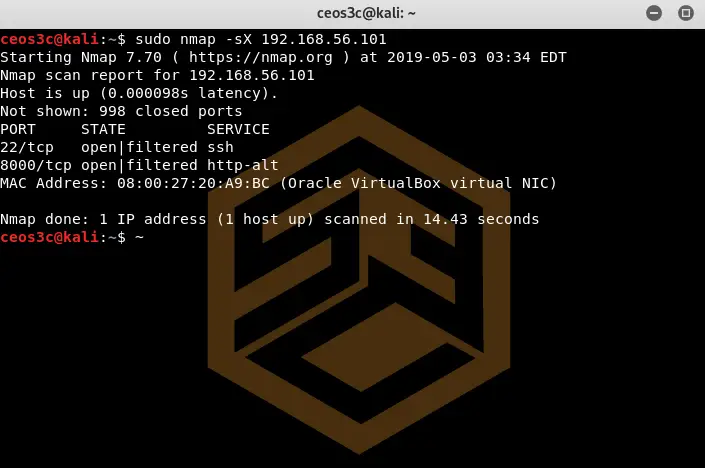
Xmas Scan (-sX)
sudo nmap -sX 192.168.56.101Code language: CSS (css)This funny-sounding scan, a quote from Nmap’s official documentation, “Sets the FIN, PSH and URG flags, lighting the packet up like a Christmas tree.” describes this scan pretty well. This is used to provoke a response from a target host behind a firewall. It’s obvious that this is a noisy approach.
TCP ACK Scan (-sA)
sudo nmap -sA 192.168.56.101Code language: CSS (css)The TCP ACK scan is used to check if a system is protected by a firewall or not. If no RST response is given from the target system, Nmap assumes that the target system is filtered. If the target system returns an RST response, it will be set as unfiltered. Ports being filtered is an indication that the system is behind a firewall. Unfiltered ports are most likely allowed through the firewall through specific rules.
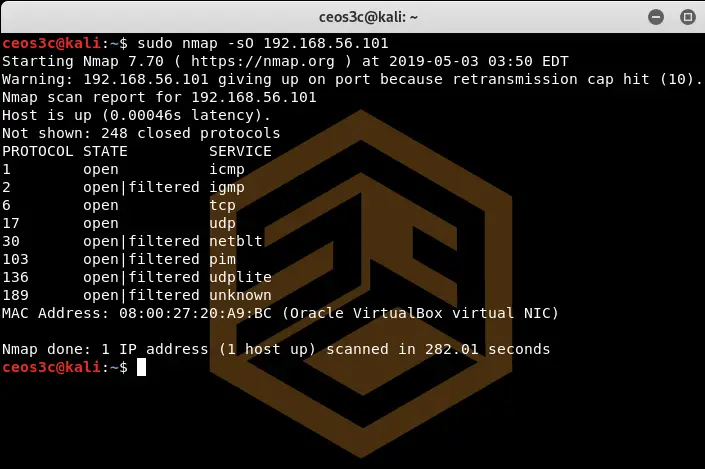
IP protocol Scan (-sO)
sudo nmap -sO 192.168.56.101Code language: CSS (css)The IP protocol scan shows all protocols that are supported by the target. This option is mostly used to determine what kind of scans you will run against the target system based on its protocols. You can find a list of all protocols here.
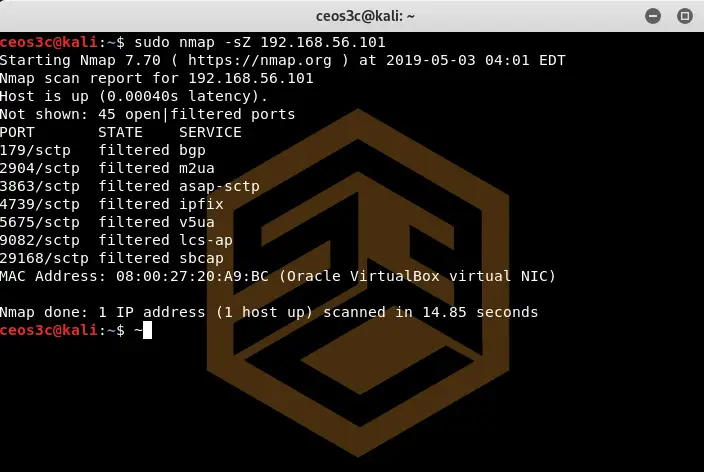
SCTP Cookie Echo Scan (-sZ)
sudo nmap -sZ 192.168.56.101Code language: CSS (css)This scan is a more advanced SCTP scan. It’s a pretty silent way of scanning because it drops packets containing Cookie Echo chunks on open ports, but it does send an Abort response if the port is closed. This scan is pretty silent, although it still can be detected by a well-configured IDS.
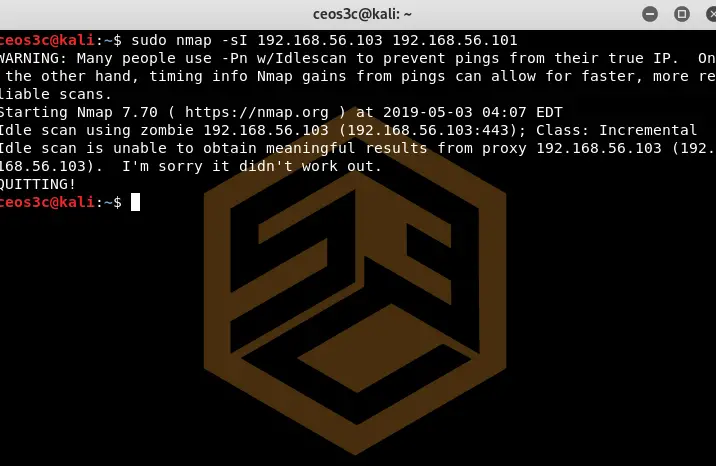
Idle Scan (-sI)
sudo nmap -sI 192.168.56.103(<--Zombie Host) 192.168.56.101Code language: CSS (css)This scanning method runs a completely blind TCP port scan against the target. There are no packets sent from your own IP address. This technique uses a so-called Zombie Host to gather information about the target. You basically specify a Zombie Host on the network that will send the packets for you, making it hard for IDS to detect your scanner.
I really like this method and use it quite often as it is really stealthy. Note that this scan does not work all the time, as you can see in my example.
Conclusion
This should give you a good of some Advanced Nmap Commands. How often you use those Nmap Commands in the real world highly depends on the scenario. Sometimes simple Nmap scans are enough to detect open ports on most systems.
👀 This Tutorial has some related Articles!
👉 Part 1 – Nmap Basics
👉 Part 2 – Nmap Host Discovery
👉 Part 3 – Advanced Nmap Commands
👉 Part 4 – Nmap NSE Scripts
👉 Part 5 – Nmap on Windows